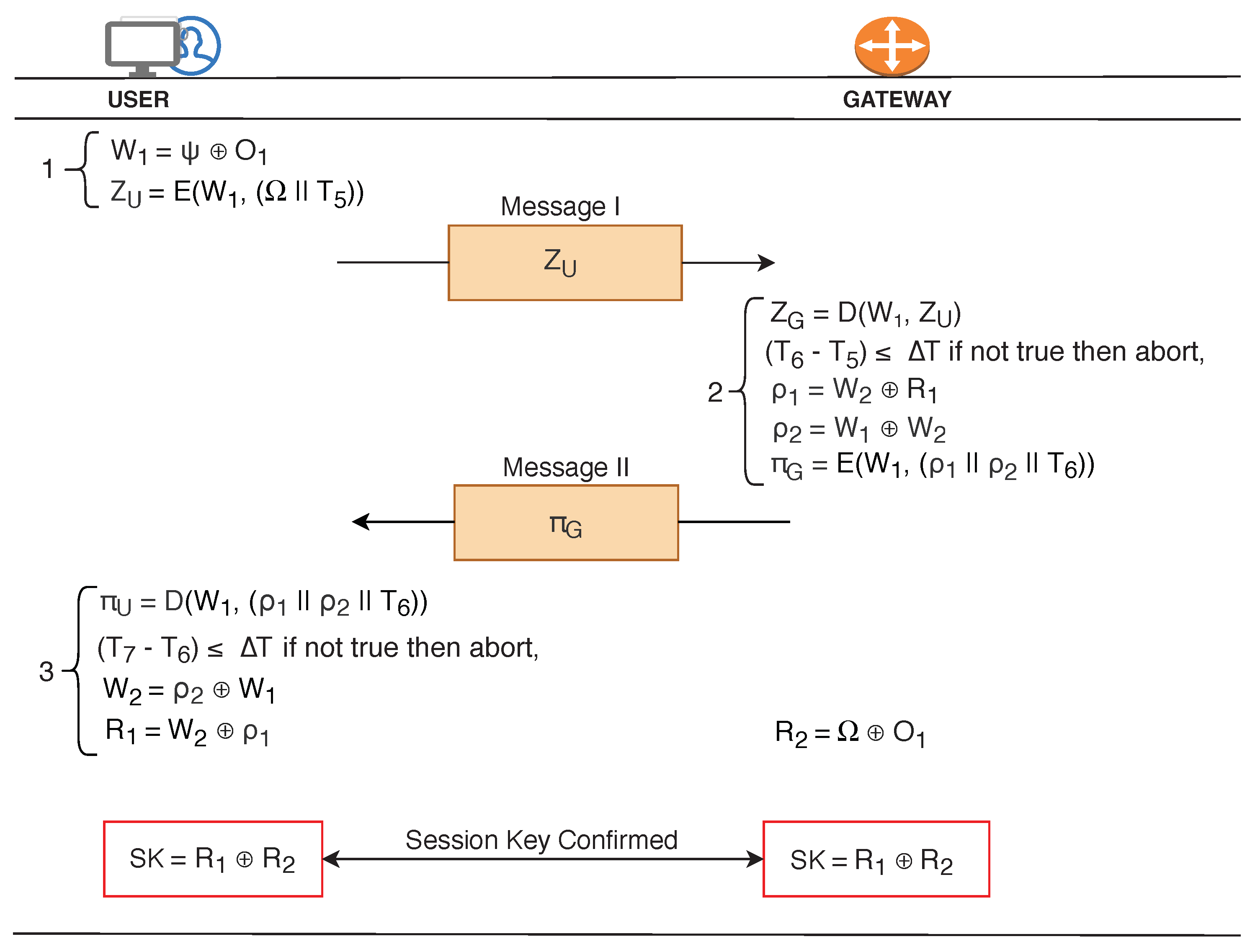
Sensors | Free Full-Text | MAKE-IT—A Lightweight Mutual Authentication and Key Exchange Protocol for Industrial Internet of Things | HTML

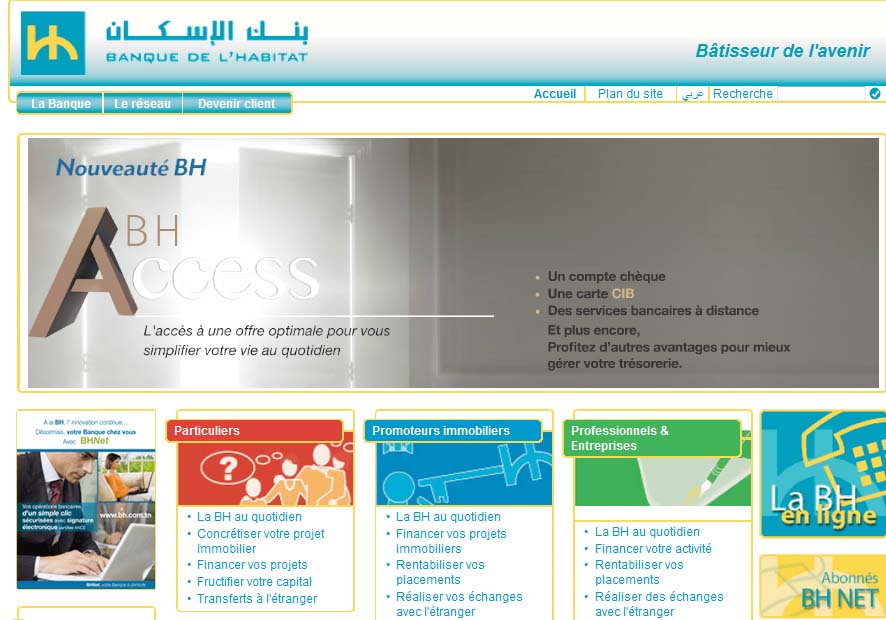
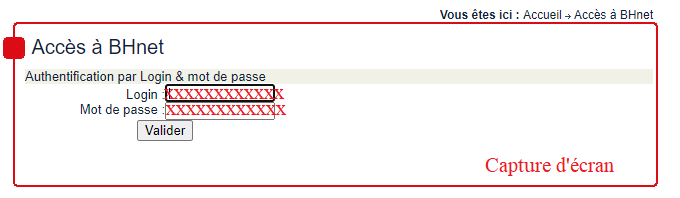
BHnet - So verbinden Sie sich mit dem BH-Netzbereich der Banque de l'Habitat - Bewertungen | #1 Quelle für Tests, Reviews, Reviews und News

A study of privacy problem solving using device and user authentication for M2M environments - Kim - 2014 - Security and Communication Networks - Wiley Online Library
VeriMark™ Fingerprint Key - FIDO U2F for Universal 2nd Factor Authentication & Windows Hello™ | Biometric Security | Fingerprint Scanner | Kensington
PLOS ONE: An Enhanced Biometric Based Authentication with Key-Agreement Protocol for Multi-Server Architecture Based on Elliptic Curve Cryptography

A secure and robust anonymous three-factor remote user authentication scheme for multi-server environment using ECC - ScienceDirect

LACO: Lightweight Three-Factor Authentication, Access Control and Ownership Transfer Scheme for E-Health Systems in IoT - ScienceDirect